In the Windows update (KB5004442), Microsoft resolved a DCOM vulnerability (CVE-2021-26414) by enforcing hardening changes that will be applied over the next Windows update. The update had been released in stages from June 2021 through March 2023, as illustrated in the timeline below:
Update release | Behavior change |
| June 8, 2021 | Hardening changes disabled by default but with the ability to enable them using a registry key. |
| June 14, 2022 | Hardening changes enabled by default but with the ability to disable them using a registry key. |
| March 14, 2023 | Hardening changes enabled by default with no ability to disable them. By this point, you must resolve any compatibility issues with the hardening changes and applications in your environment. |
What is the impact?
The DCOM update mainly impacts OPC Client applications that need to support the DCOM network Packet Level Integrity Security Changes to remotely connect to OPC Classic Servers.
The hardening changes affect the OPC Client application, when the Windows update is deployed in the OPC Server machine.
As a result, the OPC Client application code will need to be updated in case the application does not support the Packet Level Integrity Security Changes.
In many cases, such change cannot be applied at least immediately in OPC Client applications as they are part of a more comprehensive OT system such as SCADA or DCS that is running on a production environment.
Alternative and more secure solutions exist to support the Windows DCOM update and still allow remote OPC communications.
Alternative and Secure Solutions
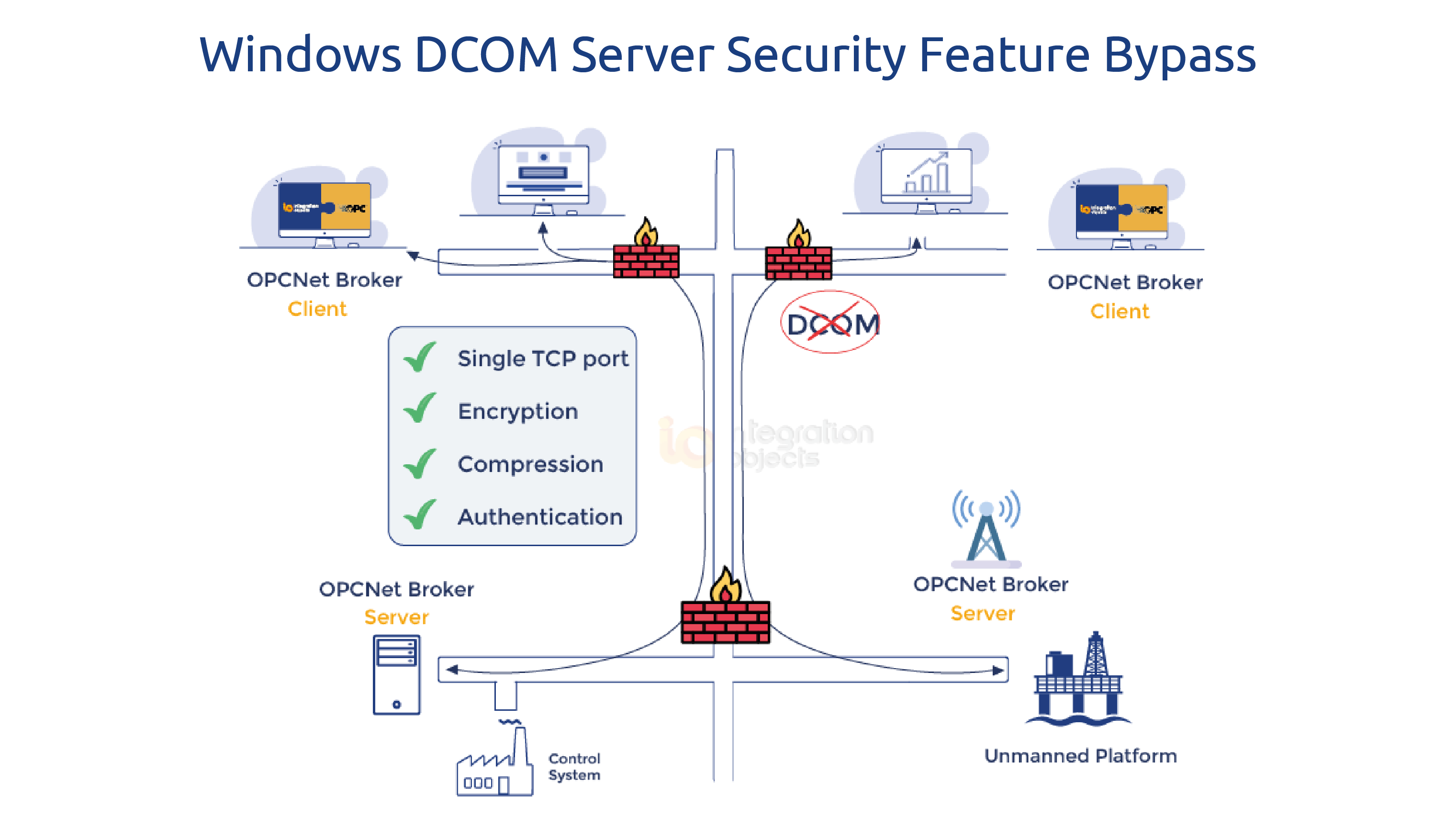
OPCNet Broker:
To avoid DCOM, its configuration and security issues, we recommend you to use our OPCNet Broker product to establish a secure tunnel between your OPC Server and Client machines.
The OPCNet Broker can securely enable OPC communication in distributed networks, through firewalls, multiple domains and by using only one TCP port for communication.
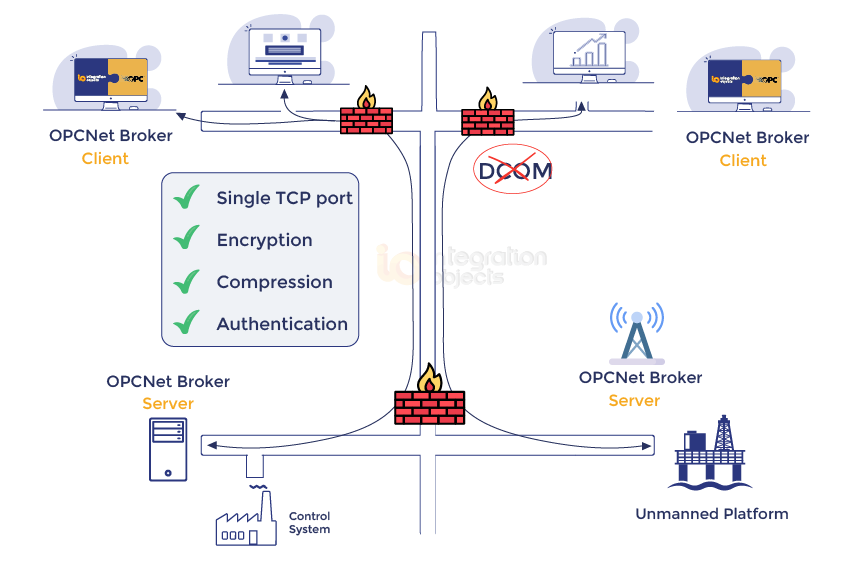
This solution will allow you to implement the Windows DCOM update while using your existing software versions for the OPC Server and Client components.Download OPCNet Broker
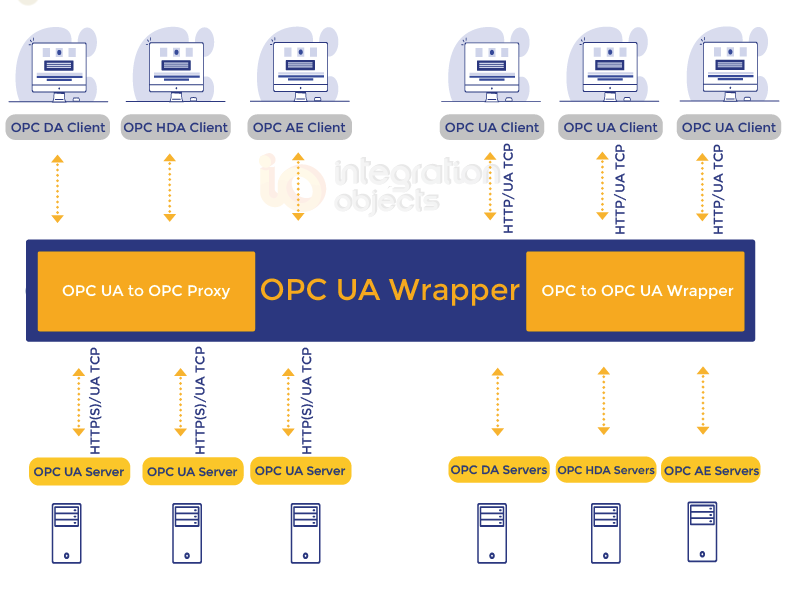
OPC UA Wrapper
When upgrading OPC Classic Client applications, several vendors chose to support OPC UA and end users tend to select this option in hope of resolving issues related to DCOM. However, users still have to maintain OPC servers supporting OPC Classic only.
To resolve such as gap and to move the connection to use OPC UA, we provide the OPC UA Wrapper product. It converts the OPC Classic Server to an OPC UA Server.
In this use case, the OPC UA Wrapper would be deployed on the OPC Server side and the remote communications between the client and server sides will be based and secured via OPC UA instead of DCOM.